If you are thinking that this is it you are absolutely wrong. Malware malicious software is a type of computer program that infiltrates and damages systems without the users knowledge.
What Is Network Security Fundamentals Of Network Security
These acts allow attackers to steal an SSID and connect without anyone being the wiser.
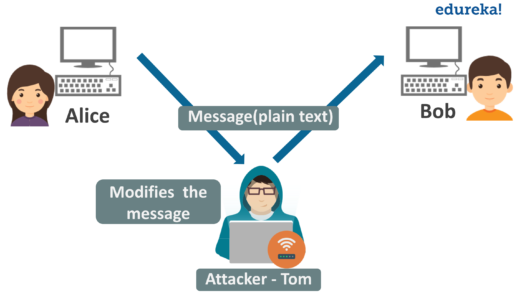
. This threat is particularly alarming as it does not rely heavily on the human element to execute and bring an organization to its knees. Unfortunately these principles mean that network traffic. Network security deals with aspects like prevention of unauthorized access termination of misuse and denial of the service problems.
You might have heard about the 2014 hacking of Sony Pictures network which the FBI attributed to the North Korean government. This aims at securing the confidentiality and accessibility of the data and network. A vulnerability is a condition of the network or its hardware not the result of external action.
Remote access to sensitive data. Remote access client devices generally have weaker protection than standard client devices. Confidentiality integrity and availability CIA.
State-sponsored espionage and sabotage of computer networks Current security technologies and best practices are not effective at preventing sophisticated targeted attacks from being successful. Many devices not managed by the enterprise No enterprise firewalls antivirus etc. These are some of the most common network vulnerabilities.
Unauthorized deletion of data. Despite the many benefits of using networks networking raises a greater potential for security issues such as. Improperly installed hardware or software Operating systems or firmware that have not been updated Misused hardware or software Poor or a complete lack of physical security Insecure passwords.
A denial-of-service DoS attack occurs when legitimate users are unable to access information systems devices or other network resources due to the actions of a malicious cyber threat actor. Exposure is different than vulnerability. Computer and network security is essentially a battle of wits between a perpetrator who tries to find holes and the designer or administrator who tries to close them.
This can help control malicious Internet traffic and often stop Trojans from downloading to your computer in the first place. Client devices in many types of environments. It provides a malicious actor with indirect access to a system or a network.
Up to 24 cash back Computer Worm A standalone malware computer program that replicates itself in order to spread to other computers Exploit operating system vulnerabilities. The importance of network security Networks operate on the principles of communication and sharing. Some are considered minor with little loss of data or monetary resources but many of them are considered major or even catastrophic.
Malicious attacks such as hacking and viruses. Though the thought process behind insider threats is gaining popularity within organizations enterprises may not always be proactive as the majority of network security defenses are configured to protect from external threats. Add another line of defense for your network by keeping your Internet connection as secure as possible and always keeping a software and hardware firewall up at all times.
Describe the security issues surrounding the use of computer networks describe other issues such as the internet is not policed and the effects of. Network Security refers to the measures taken by any enterprise or organisation to secure its computer network and data using both hardware and software systems. Network-based ransomware can cripple systems and data.
Security may be referred to as complementing factors like. Remote access client devices may be used in hostile environments but not. These measures also enable the safe operation of IT systems.
By connecting computers it is possible to share personal data easily. Services affected may include email websites online accounts eg banking or other services that rely on the affected computer or network. Worms typically cause harm to their host networks by consuming bandwidth and overloading web servers.
It refers to a set of rules and configurations designed to protect the integrity confidentiality and accessibility of computer networks and data. Keeping track of others computer system activities illegally. You can implement measures to reduce your networks.
Different types of Network Threats. Hacking id passwords of the users etc. A novice user can quickly set up one of these devices and gain access or open up a network to external use without further configuration.
Trojan Horse A program designed to breach the security of a computer system while. An exposure could enable a hacker to harvest sensitive information in a covert manner. Computer security breaches are commonplace and several occur around the world every day.
Insider abuse can include but is not limited to. Sound network security controls are recommended for organizations to reduce the risk of an attack or data breach. Malware tries to go unnoticed by either hiding or not.
Lack of physical security controls. Network security Computer networks have many benefits but they also create security risks. Encryption essentially gives hackers free rein to operate prior to their eventual detection and remediation.
Other potential issues with configuration include weak passphrases feeble security deployments and default SSID usage. The great advantage that the attacker has is that he or she need only find a single weakness while the designer must find and eliminate all weaknesses to achieve perfect security. The non-physical threads can be commonly caused by.
What Is Network Security Fundamentals Of Network Security

Network Security Threats 5 Ways To Protect Yourself



0 Comments